Avoiding HIPAA violations goes beyond air tight technical system controls. Often the leaks and violations come through the human elements of healthcare operations.

To improve the efficiency and effectiveness of the health care system, the Health Insurance Portability and Accountability Act of 1996 (HIPAA), Public Law 104-191, included Administrative Simplification provisions that required HHS to adopt national standards for electronic health care transactions and code sets, unique health identifiers, and security.
At the same time, Congress recognized that advances in electronic technology could erode the privacy of health information. Consequently, Congress incorporated into HIPAA provisions that mandated the adoption of Federal privacy protections for individually identifiable health information.
“Under HIPAA, protected health information is considered to be individually identifiable information relating to the past, present, or future health status of an individual that is created, collected, or transmitted, or maintained by a HIPAA-covered entity in relation to the provision of healthcare, payment for healthcare services, or use in healthcare operations.”
– HIPAA Journal
Avoiding HIPAA Violation: 10 Most Common Violations
- Snooping on Healthcare Records
- Failure to Perform an Organization-Wide Risk Analysis
- Failure to Manage Security Risks / Lack of a Risk Management Process
- Denying Patients’ Access to Health Records/Exceeding Timescale for Providing Access
- Failure to Enter into a HIPAA-Compliant Business Associate Agreement
- Insufficient ePHI Access Controls
- Failure to Use Encryption or an Equivalent Measure to Safeguard ePHI on Portable Devices
- Exceeding the 60-Day Deadline for Issuing Breach Notifications
- Impermissible Disclosures of Protected Health Information
- Improper Disposal of PHI
Non-Financial HIPAA Violation Examples
- Emailing ePHI to Personal Email Accounts and Removing PHI from a Healthcare Facility
- Leaving Portable Electronic Devices and Paperwork Unattended
- Releasing Patient Information to an Unauthorized Individual
- Releasing Patient Information Without Authorization
- Disclosures of PHI to Third Parties After the Expiry of an Authorization
- Impermissible Disclosures of Patient Health Records
- Downloading PHI onto Unauthorized Devices
- Providing Unauthorized Access to Medical Records
Details and examples for each violation can be found: https://www.hipaajournal.com/common-hipaa-violations/
HIPAA Cases and Punishments: https://www.hipaajournal.com/hipaa-violation-cases/
Enforcement Process
HHS’ Office for Civil Rights (OCR) is responsible for enforcing the Privacy and Security Rules. Enforcement of the Privacy Rule began April 14, 2003 for most HIPAA covered entities. Since 2003, OCR’s enforcement activities have obtained significant results that have improved the privacy practices of covered entities. The corrective actions obtained by OCR from covered entities have resulted in systemic change that has improved the privacy protection of health information for all individuals they serve.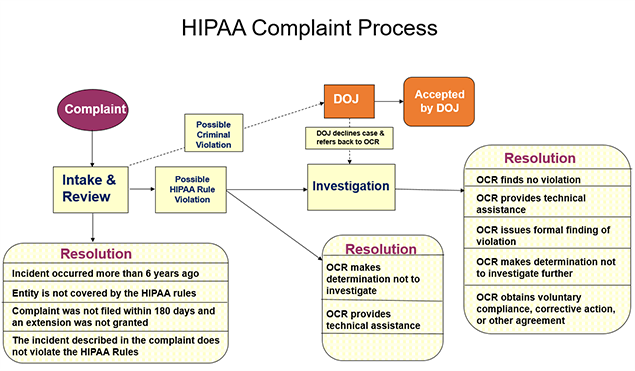
OCR enforces the Privacy and Security Rules in several ways:
- by investigating complaints filed with it,
- conducting compliance reviews to determine if covered entities are in compliance, and
- performing education and outreach to foster compliance with the Rules’ requirements.
OCR also works in conjunction with the Department of Justice (DOJ) to refer possible criminal violations of HIPAA.
How OCR Enforces the HIPAA Privacy & Security Rules
OCR is responsible for enforcing the HIPAA Privacy and Security Rules (45 C.F.R. Parts 160 and 164, Subparts A, C, and E). One of the ways that OCR carries out this responsibility is to investigate complaints filed with it. OCR may also conduct compliance reviews to determine if covered entities are in compliance, and OCR performs education and outreach to foster compliance with requirements of the Privacy and Security Rules.
How OCR Enforces HIPAA Privacy
Download our informative flyer on Medical Necessity Criteria by completing this form.
| |
| Editor’s Note: BHM Healthcare Solutions offers a premier network of behavioral health peer reviewers ready for your cases. Our physician network forms the foundation for a wide range of review services. CLICK HERE and we can discuss how our peer-to-peer connection rates and clear member statements set BHM apart. |