“If data is everywhere, how do you protect it?”
This thought has been on my mind well before the Change Healthcare hacks (that’s plural) with which U.S. health care stakeholders are still dealing as this post goes live on the Health Populi blog.
It’s a question posed to me in conversation with Richard Kaufmann, Chief Information Security Officer (CISO) with Amedisys. I’m grateful for the opportunity to explore in depth the many facets of cybersecurity in health care with Richard – the growing threats, the impact on providers, the state of technology and innovations to manage risks, and his evolving role as a CISO in this challenging context.
Our conversation covered so much ground, I’ve divided it into three posts: this one focused on Richard’s “origin story” in information security and Amedisys’s approach to the enterprise’s cybersecurity strategy; then, I will publish parts 2 and 3 in each of the next two months, to look into Amedisys’s plan and implementation of its current security infrastructure and strategy and lessons learned in the process. Finally, we’ll post the last third of our conversation. looking back and looking forward to the future of cybersecurity in health care and some wisdom to help us manage that future world of risks.
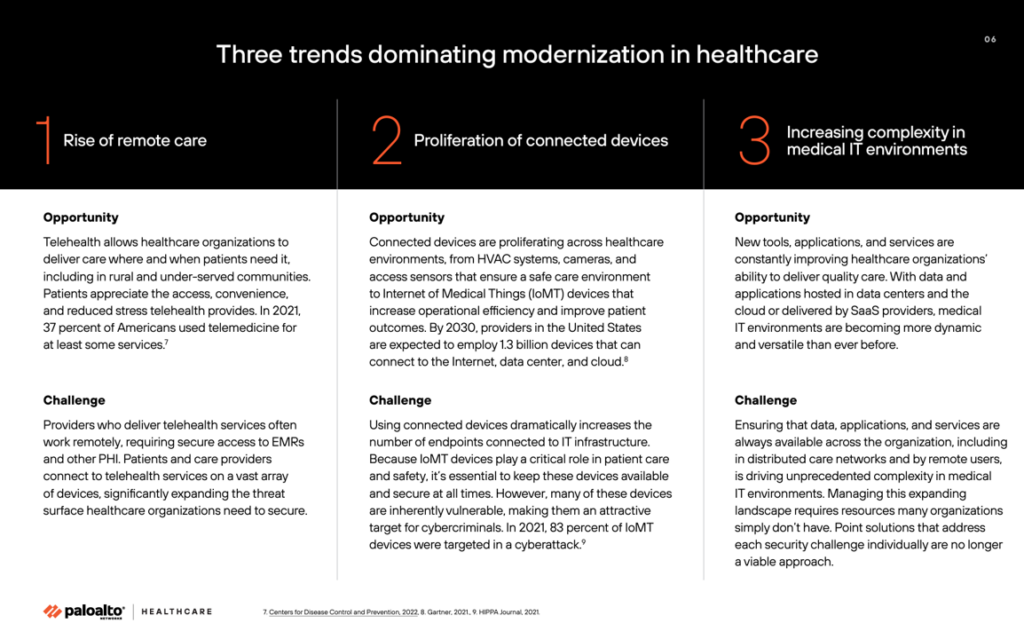
As we embark on our healthcare cybersecurity journey with Richard Kaufmann, consider three trends suggested by Palo Alto Networks that will challenge the industry to devote more time and energy to addressing growing risks of hacks and breaches:
- The rise of remote care, especially relevant to home care, telehealth, palliative and hospice care
- The proliferation of connected devices, such as remote health monitoring, Internet of Things for health (especially at home), and other applications that can connect to the Internet, the data center and the cloud, and,
- Increasing complexity in medical IT environments in distributed care networks and across remote users.
With that evolving cyber-risk healthcare landscape in mind, I now welcome into my conversation with Richard Kaufmann, CISO of Amedisys, Part 1 – Origin Stories, the Security Ecosystem, and the Start Line…(note that my questions are in italics, and Richard’s voice in plain font).
JSK: What’s your origin story with health information security? When you started working with Blue Cross and Blue Shield of Louisiana over a decade ago, was cybersecurity on your mind?
RK: I’ll go ahead and date myself here. I was born in the early 80’s and grew up alongside the internet. The internet was such a different experience when I was a teenager and in many ways it almost felt manageable. As a teen being raised in Southeast Louisiana, being able to connect with others in chat rooms and forums exposed me to a world view that was incredibly impactful to myself as an adult.
The early “hackers” were idealists. The online communities that resonated with me were all about leveraging this new tool called the internet to make the world a better place. Hacking back then felt more mischievous than criminal, and it was easily justifiable for the greater good.
By the time I arrived at BCBSLA as a young professional, most of the light heartedness of cybersecurity had long since faded and idealism was replaced by profiteering. Doing things for “the lulz“ had been replaced with doing things for the dollars; now the gratification I got from being online was using my skills to better understand what the “bad guys” were doing.
I kind of came through the side door of cybersecurity as a profession. My career started as a network engineer and then pivoted to Internal Audit of all places. Internal Audit is uniquely positioned in an organization and getting the opportunity to see how a company operates and, most importantly, how C-Suites prioritize solutions, has been one of the best decisions I’ve made on the road to becoming a CISO.
JSK: You moved into the Amedisys organization in 2018 as Chief Information Security Officer. What has changed in the environment for cyber-security since you took on that role?
RK: Collaboration has been forever transformed in a post-COVID world. One of the biggest byproducts of this change is that organizational data has become ambient. For highly regulated industries like healthcare, cybersecurity and data protection go hand in hand. If data is everywhere, how do you protect it? At Amedisys, we start answering that question by respecting where the data originates from.
As a patient moves through the continuum of care, we understand and value that our patients’ experiences are private. Individuals have a fundamental right to dictate who and when their health information is leveraged.
Working to keep that information private in the new paradigm of Teams Meetings, PowerBI reports, and decentralized data is a heavy burden for modern CISOs. An added complication is that CISOs aren’t just trying to keep information away from adversaries who want to exchange privacy for profit, but also from accidental disclosure in the normal course of doing business.
JSK: Tell us how cyber-security challenges might be different for Amedisys in the home health, hospice, and palliative care world compared with other health care service environments like inpatient care or medical group practices.

Amedisys is one of the largest providers of Hospice and Home Health in America. As a comparison, one of the largest hospitals has a little over 2,000 beds, whereas our company provides care for over 400,000 patients each year. We have all the challenges of a traditional hospital because we provide similar services, but with the extra variable that we provide care from patients’ homes.
Providing care in the home adds some complexity to cybersecurity, specifically when you think of things like connectivity, or lack thereof. We do our best to see the world through our patients’ eyes, while also ensuring our clinicians’ safety. Imagine having a loved one with dementia that may not remember why a caregiver is knocking on their door for a home health visit. Ensuring our clinicians are safe while also being able to provide an industry-leading level of care is where our organization thrives.
JSK: As you look back on the “starting line” for planning and implementing Amedisys’s cyber-security strategy, what were the key considerations and challenges you had on the front-burner for your project?
RK: At Amedisys, regardless of your job title, everyone is a caregiver. That’s more than just corporate culture jargon for us. Everyone in our organization approaches their job function from a place of: “How can I improve someone else’s experience through my actions?” Our security strategy is anchored in compassion, empathy, and helpfulness. It’s amazing the things you can accomplish as a cybersecurity capability when you put your patients or customers first.
One of the most impactful experiences of my career was working with our hospice nurses during the height of COVID. Hospice is a service that isn’t leveraged enough in our country. It is an uncomfortable subject to discuss – the transition from life to death. Our hospice nurses overcome this uncomfortableness daily. Hospice is also the sole healthcare service where the goal isn’t to make someone healthier, but to improve their quality of life.
In many ways, it feels like we’ve blocked out how scary the early days of COVID were. Before the idea of “flattening the curve” or even quarantining with our sourdough starters and distraction of “Tiger King,” people were actively dying from the disease.
Hospice nurses showed up every day just so their patients, some of them carrying a highly infectious disease, were comfortable in their final days. Going to work meant putting themselves in harm’s way—and they still did it. Collectively, the hospice nurses at Amedisys during COVID were the most brave and selfless individuals I’ve ever met.

I can remember shortly after our organization finalized our Teams adoption and I met with a hospice leader and asked – what does your team need? I’ll never forget the response: “We need hugs.”
COVID had completely isolated a group of our employees who needed community. They needed to grieve. They needed to vent. They needed a place where their experience as humans could persist, even after working hours.
Being able to set up online communities as well as communication avenues where this group of employees could console each other was an incredibly fulfilling experience. Sure, we worked to make those things secure and that the data and experiences that were shared remained private, but more importantly technology was truly uniting people when they needed it the most.
JSK: I’ve heard you talk about the importance of the ecosystem in your approach to cyber. Can you explain?
RK: As much as we try to make being a CISO a conversation about security, it’s about aligning company objectives with keeping data private in the most effective way possible. There’s a balancing act here between cost and value.
I haven’t met a CISO yet who has presented a plan to make things more secure and has a 100% success rate in getting the funding for that idea. We are constantly being challenged to reduce costs.
I approach technology ecosystems the same way I approach getting my kids to eat dinner. Every single one of them is going to have different requirements and an idea of what’s best for them at that moment. Chicken nuggets, pizza, tacos (the latter only on Tuesdays, obviously). To them there is no limit to the resources available. However, as a parent and as a CISO, it’s my role to reconcile what is really needed against the resources available. In my experience, the best way to do that is to go to a single place that offers the most variety.
Lately, Amedisys has been investing heavily in the Microsoft Security Stack because of that very reason. Not only do the individual products meet our requirements, but there is added simplicity in those security products having native functionality to our productivity suite. Additionally, our team is passionate about improving the products we use and having a single escalation point means that we can see improvements across the enterprise, even if our feedback is focused on a specific capability.

JSK: I read somewhere that you sometimes summon up David Goggins, the endurance athlete, during your hikes and other fitness efforts. Interestingly, Goggins works in his spare time as an emergency technician in British Columbia where he lives. What can you take from Goggins’ inspiration into your “marathon” of cybersecurity work with Amedisys?
RK: There are two concepts that really resonate with me when I look at people like Goggins. The first is having the ability to self-rescue. No one is coming to help you. That’s a hard lesson to learn and not everyone grasps it. When I coach other CISOs, that’s one of the cornerstones of how I approach leadership. The best team leaders are great team members first. Being a great team member is being able to hold yourself accountable. If you want to do 100 pull-ups, you start by doing 1 and understand that no one else is doing the other 99 for you. Self-sufficiency and accountability are soft skills that allow our security team Amedisys to thrive, even with a limited number of headcounts.
The second concept is the difference between motivation and discipline. Motivation fluctuates. There are good days and bad days – it’s dynamic. When things are dynamic in security, that’s when holes are created. Having the discipline to tackle tasks, regardless of size or desire to complete them, helps us keep a stable operating environment that our operational teams can leverage. Discipline provides us a path to becoming comfortable with being uncomfortable.
And so we’ve journeyed from the early mischievous days of hacking to moving to the “other side” of the cyber-equation to the specific landscape of health care delivered at home collaborating with patients and caregivers – with technology only one part of a longer recipe that bakes in empathy, community, and hugs – on a marathon with inspiring role modeling discipline from David Goggins.
Stay tuned for Part 2 of this 3-part exploration into cybersecurity and health care with Richard Kaufmann, CISO of Amedisys, and me, to be published in mid-June…




 Thanks to Feedspot for identifying
Thanks to Feedspot for identifying  Jane was named as a member of the AHIP 2024 Advisory Board, joining some valued colleagues to prepare for the challenges and opportunities facing health plans, systems, and other industry stakeholders.
Jane was named as a member of the AHIP 2024 Advisory Board, joining some valued colleagues to prepare for the challenges and opportunities facing health plans, systems, and other industry stakeholders.  Join Jane at AHIP's annual meeting in Las Vegas: I'll be speaking, moderating a panel, and providing thought leadership on health consumers and bolstering equity, empowerment, and self-care.
Join Jane at AHIP's annual meeting in Las Vegas: I'll be speaking, moderating a panel, and providing thought leadership on health consumers and bolstering equity, empowerment, and self-care.