Technology risk management itself is not a new concept, but its requirements have evolved alongside the actual technologies we now use to run businesses. Decentralized systems, rapid software implementations, larger application portfolios — all of this and more makes IT risk and security management a priority not only for IT teams but business leaders across the enterprise.
Today, a single negative security event can cost millions of dollars to recover from. And while security breaches are never totally avoidable, a solid technology risk management strategy can reduce its adverse impact on a business.
This post offers a guide on technology risk management, what it means in practice, and how connecting enterprise architecture to your strategy can have real security benefits.
Quick Takeaways
- Technologies like cloud computing, microservices, and IoT have increased the potential that companies will experience IT security events.
- A technology risk management strategy typically includes assessment, evaluation, and maintenance of security risks.
- Enterprise architecture management can support technology risk management through increased visibility, better end-of-life management capabilities, and processes for IT standardization.
The State of Technology Risk in 2022
The implementation of any technology always comes with a certain level of risk. That risk, however, has become increasingly complex as technologies like cloud computing, microservices, and IoT devices have created decentralized IT infrastructures and broader attack surfaces for cyberthreats.
Data breaches increased significantly for both small and large businesses in the U.S. and Canada between 2020 and 2021 (shown in the graph below) — and this is only one type of IT security event. Consider also the threat of malware attacks, outages, and misconfigurations and it’s clear why technology risk management is a priority for businesses of all sizes.
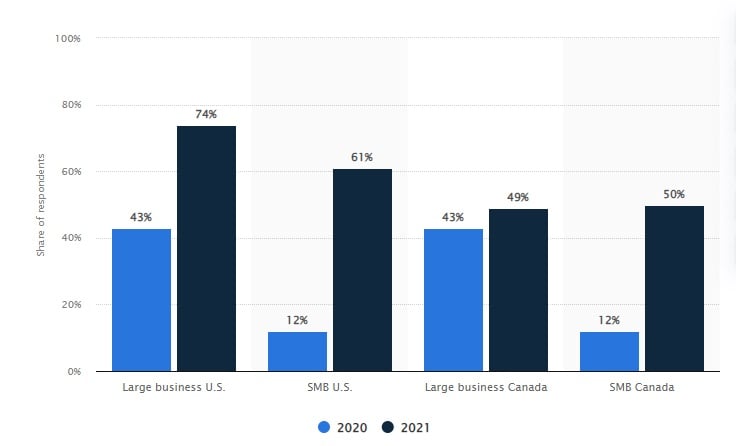
Data breaches, a common technology risk today, rose significantly between 2020 and 2021 for both small and large businesses (source).
At the same time, more traditional security concerns like internal compliance and end-of-life technology management have become more challenging as enterprises use more applications (as many as 650 for the average large enterprise and up to 3400 for the largest 10%) and other IT components.
Companies must think more proactively and strategically about technology risk management, implementing collaborative approaches to its execution that secure the enterprise and allow it to operate with necessary levels of agility.
What does technology risk management actually mean?
Given its importance to business success, it is worth defining technology risk management more specifically and outlining exactly what’s involved in its execution.
In general, technology risk management activities can be grouped into one of the following three categories:
- Assessment - The initial step in any technology risk management strategy, which includes listing all IT assets (software, hardware, networks, etc.) and associated risks.
- Prioritization - Evaluating risks to understand their urgency and level of importance, then prioritizing the order and/or extent to which they’ll be addressed
- Maintenance - Ensuring that ongoing security best practices – like access control or data privacy compliance – are being followed
All three activities are important to maintaining needed levels of security in the modern enterprise, and they all require collaboration between risk and IT teams as well as other stakeholders (end users, department managers, and legal/compliance teams to name a few).
The Benefits of an EA-Driven Approach to Technology Risk Management
A less commonly mentioned but critical contributor to effective technology risk management is the enterprise architecture team. EA teams possess both a global and a granular perspective on critical infrastructure, with the ability to zoom in or out as needed to assess risk and determine the best course of action to address it.
Further, EA teams manage powerful data resources that can be shared with risk managers across the enterprise to drive better IT management and lower overall risk. Let’s look at 4 ways an EA-driven approach to technology risk management can benefit organizations.
Risk visibility
As mentioned before, the first step in a technology risk assessment is to list IT assets and fully understand your current state architecture. EA platforms typically hold this information and make it available for teams who need it. Even better, these platforms can make it available in the form of landscape maps, diagrams, business capability maps, or other visualized formats so it’s easily digestible and analyzable.
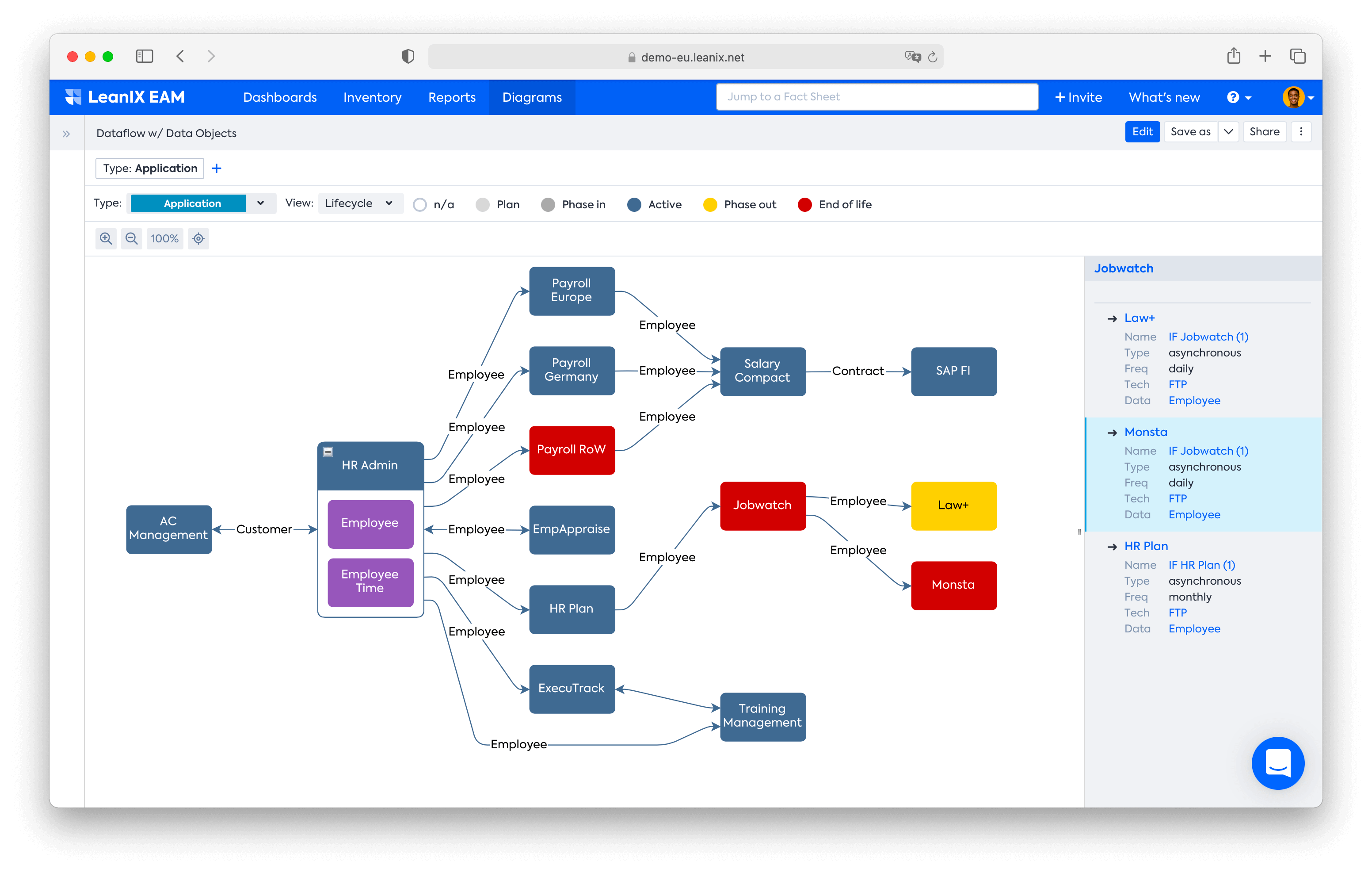
Dataflow Diagram example created in the LeanIX platform.
Better end-of-life asset management
Technology assets approaching obsolescence present a higher risk for security vulnerability. In fact, more than a third of security breaches are caused by outdated technologies. An enterprise unequipped to manage the technology lifecycle (end-of-life assets) opens itself up to higher security risk, especially from threat actors seeking out old systems.
Enterprise architecture tools give you continual, real-time insight into which applications and assets are nearing obsolescence so that enterprises can proactively plan to phase them out and replace them.
As you can see in the LeanIX Application Landscape report below, it’s easy to spot end-of-life applications (red) and/or those that need to be phased out (yellow).
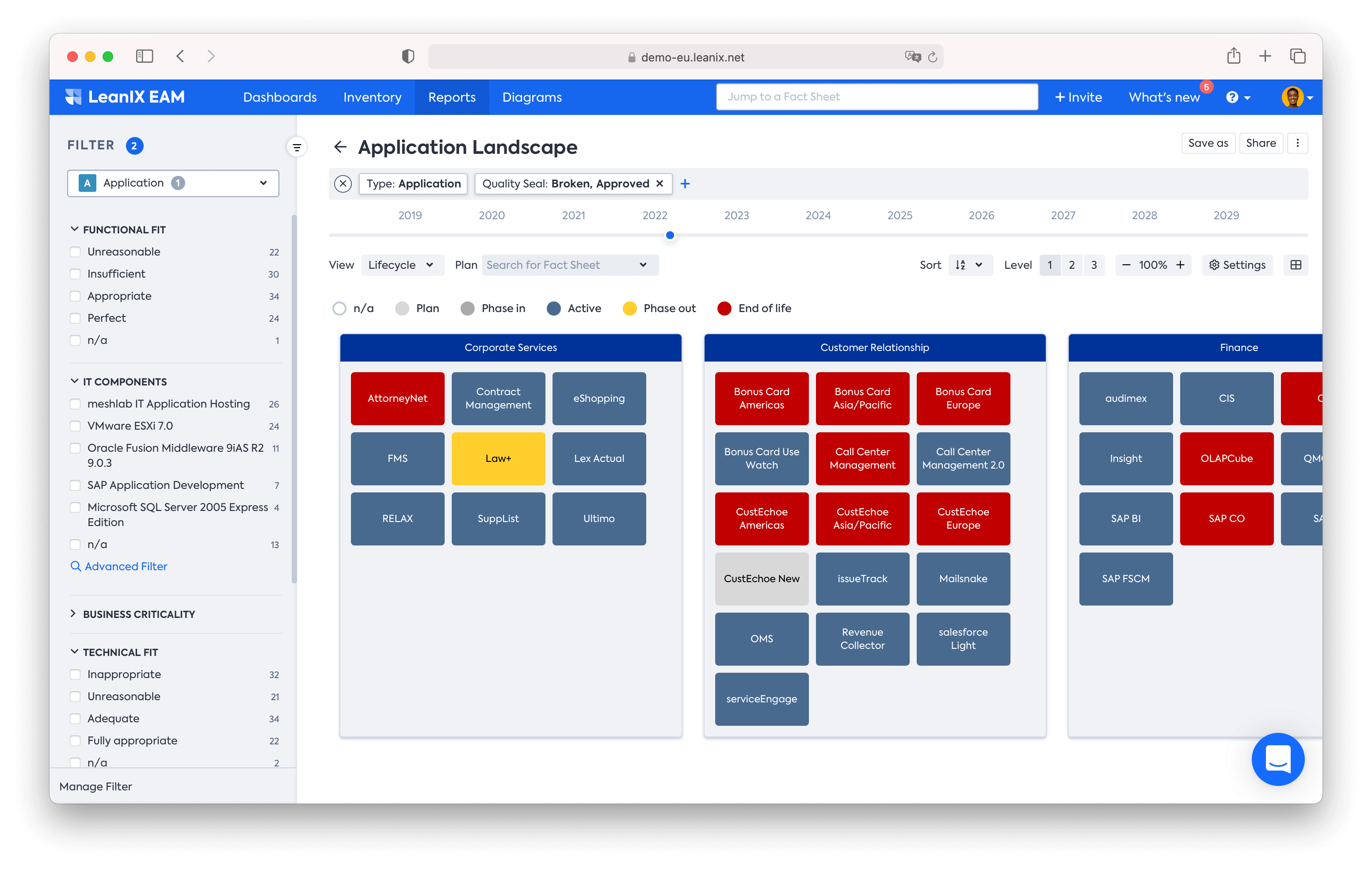
Application Landscape Reports boost technology risk management capabilities with real-time visualizations.
Standardization
It’s generally said in the IT world that more than half of IT security breaches come from insider threats — employees or other internal stakeholders who (intentionally or not) put a company at risk by compromising data, breaking access control rules, or similar action.
It’s critical, then, to pursue standardization when it comes to application access, data access, and sharing information. EA tools inform standardization by serving as a central source of truth for information regarding application ownership, licenses, approved users, use cases, process standards and more. The data EAs collect plays an essential role in efforts aimed at lowering the risk of an insider security threat.
Increased agility through informed decision making
Real-time access to application portfolio information — including dependencies and other relationship paths — allows business leaders at an organization to make technology decisions with a full understanding of their security implications.
This prevents business leaders from creating inadvertent risk when turning systems on and off. And by exposing potential threats that would otherwise go unnoticed, it elevates overall security awareness at the leadership level.
Manage technology risks with confidence using LeanIX
LeanIX can help you identify, evaluate, and mitigate risk using reports purposed specifically for technology risk management. Using the LeanIX platform, you can:
- Build a technology inventory as a foundation for effective risk management
- Synchronize data with ServiceNow or other ITSM solutions
- Use LeanIX’s built-in lifecycle catalog for lifecycle maintenance
- Uncover and evaluate obsolescence risk
- Plan and track risk mitigation
Schedule a call with us to get started.

/EN/Reports/Thumbnail-Obsolescence-Gartner.png?width=140&height=100&name=Thumbnail-Obsolescence-Gartner.png)
/EN/White-Paper/EN-IDC-Inforbrief-Application-Rationalization-Portfolio-Management-Thumbnail_v2.png?width=140&height=99&name=EN-IDC-Inforbrief-Application-Rationalization-Portfolio-Management-Thumbnail_v2.png)